Your own private little locker - Truecrypt
Whether you're at home or on the go, there is some data you just don't want publicly available. Employing a login password on your computer is one way to go about its protection, but what about if someone gets really smart and uses a boot disk?In this one instance, Linux security is actually less than a similar Windows box - drop in a Knoppix CD, boot up, and mount the hard drive like it was your baby. Of course, thanks to the previously mentioned way Windows stores passwords, that's actually about two steps less than you'd have to do to get the actual passwords on a Windows system. Linux has the hash file to protect its passwords, at least.
Unfortunately, all the passwords in the world do little to protect anything but operating system access in most setups. Though this makes a formidable protection from the likes of most hackers trying to get at your data remotely (who then must operate within the OS), it means that local data is all too readily accessible. This also includes USB keys, where your Portable Firefox/Mozilla/PuTTY setup resides. That's not always a good thing to let just anyone get his or her mitts on.
To counteract this threat, there is the encrypted volume. An encrypted volume is exactly that - a partition of space that is automatically encrypted and decrypted on the fly. Dropping a file in the volume encrypts it, running it will decrypt on the fly (leaving only traces in memory) - for all intents and purposes it works like any other volume. Until it's unmounted, that is...and suddenly it's just a big blob of random mess.
Encrypted volumes aren't necessarily a "new" concept, but they've only recently been given the careful design attention that they deserve. The best program for the job is Truecrypt, an absolutely brilliant open-source encrypted volume manager. To my surprise, Corsair thought ahead and put a copy of the software on each of its new Flash Voyager GT drives. I've been using it for some time, but it was a very welcome sight to see a big company taking this seriously.
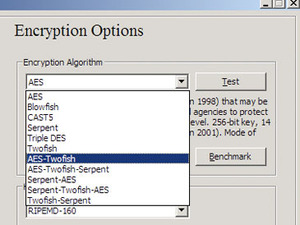
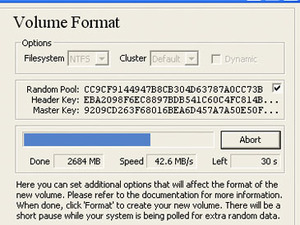
I personally like the option of being able to use files as part of my key, meaning the volume could simply fail to open if I don't copy a file to a particular location or I'm not on my host computer. Or, one file present can open one set of info while another is required for the real data. Truecrypt uses a combination of both the name and the file size, so it can't be spoofed by fakes, either.
It has a very low memory requirement, though it does require Administrator access on the host computer in Windows to allow mounting volumes (the Linux variant has no similar requirement for root privileges). Fortunately for most of us, a vast majority of Windows computers have their local accounts set to Administrator privileges, even if their network accesses are controlled. That's not so much a fault of Windows as lazy software design, since many business programmers don't write programs in a way that doesn't require access to certain "privileged" parts of the system.
Though Microsoft Windows Vista comes with a similar system, called BitLocker, that only appears on the "Ultimate" version of the software and it is limited to the computer it is installed on. In the meantime, Truecrypt is free to take with you anywhere you go. This way, you can spread the love of privacy, not your private data.
Mail bomb - PGP
No discussion on cryptography worth its salt could go without mentioning the daddy of all business crypto, PGP. For anyone who has been living under a rock since 1991, PGP stands for "Pretty Good Privacy," and that's exactly what it is. Over the years, PGP has turned into a pretty frilly, bells-and-whistles application with lots of little extras. However, at its heart it is still the good old asymmetric-key cipher program that's been keeping mail safe for over 15 years.
Corporate-level PGP takes on open source GPG.
PGP was completely freeware for quite a few versions before the guys who held the patent to RSA caught on. At that time, Philip Zimmermann, the software's creator, was forced to sell at least a commercial version for business users to pay the royalty charges. Since then, PGP has grown to be a very large company, though freeware versions of the software for personal use have largely been discontinued since 2002. However, you can still find them and they still do work just as well as they ever did (or you can grab GPG, an open source version).
The new paid-for suite comes with the ability to encrypt small files as well as emails, making it good for sending attachments with a little more security than your average ZIP or RAR file. It also comes with a shredder for deleting more personal data without leaving the normal traces that Windows does.
Unfortunately, much like Truecrypt, it looks like most of the versions require a full install rather than just being able to be run straight from the USB key. However, I've not checked out all of the versions out there - so if someone spots one, please let us know!

MSI MPG Velox 100R Chassis Review
October 14 2021 | 15:04









Want to comment? Please log in.